Private Status Page
Private Status Pages are similar to External Status Pages, but only authorized users are allowed to access them. Private Status Pages are not available to the general public. Authorization is handled by OpenID SSO, and is independent from PagerDuty's Single Sign-On (SSO) feature.
Pricing Information
PagerDuty offers two Status Page packaging add-on options, one which includes Public Status Pages, and a premium package that also features Private Status Pages and Audience-Specific Status Pages. Depending on the package you choose, features such as Page Subscribers, Premium Account Subscribers, and Total Account Subscribers may vary.
Please contact our Sales Team for more information.
Create a Private Status Page
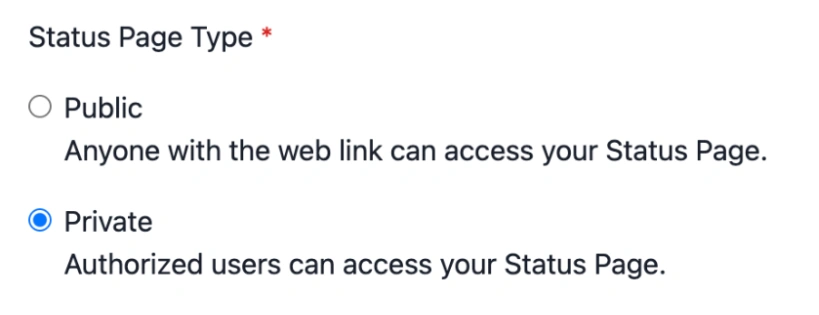
- In the PagerDuty web app, navigate to Status External Status Page.
- ClickNew Status Page and, under Status Page Type, select Private.
Initial setup
- Continue setting up the status page using the instructions from Create an External Status Page.
Prerequisites for Single Sign-On (SSO)
Before configuring Single Sign-On for your Private Status Page, review the following requirements to ensure a smooth setup process.
Identity Provider Compatibility
OIDC Application Support
Verify that your IdP subscription or plan includes OIDC application support. Some providers restrict this functionality to specific pricing tiers or enterprise plans.
Your identity provider (IdP) must support the OpenID Connect (OIDC) protocol with the authorization code flow. PagerDuty's Private Status Pages have been tested and verified to work with the following identity providers (but not limited to):
- Okta
- Azure AD (Microsoft Entra ID)
- Salesforce
- Ping Identity
Administrative Access
You'll need administrative access to your identity provider with sufficient privileges to:
- Create new OAuth 2.0/OIDC applications
- Configure application settings and callback URLs
- Manage client credentials (client ID and client secret)
- Define custom claims and user attributes
Required OIDC Scopes
PagerDuty will request the following standard OIDC scopes during authentication:
- openid — Required for OIDC authentication
- email — Used to identify and match users
- profile — Provides basic user profile information
Ensure your identity provider is configured to support and return these scopes.
Custom Claim Requirement
Your identity provider must support sending a custom claim named status_pages in the ID token or Access token response. This custom claim should contain the identifier(s) of the Private Status Pages(s) a user can access.
Configure Single Sign-On (SSO)
You will need to configure SSO on your Private Status Page before users can access it. Private Status Pages use the OpenID Connect (OIDC) protocol to allow users access.
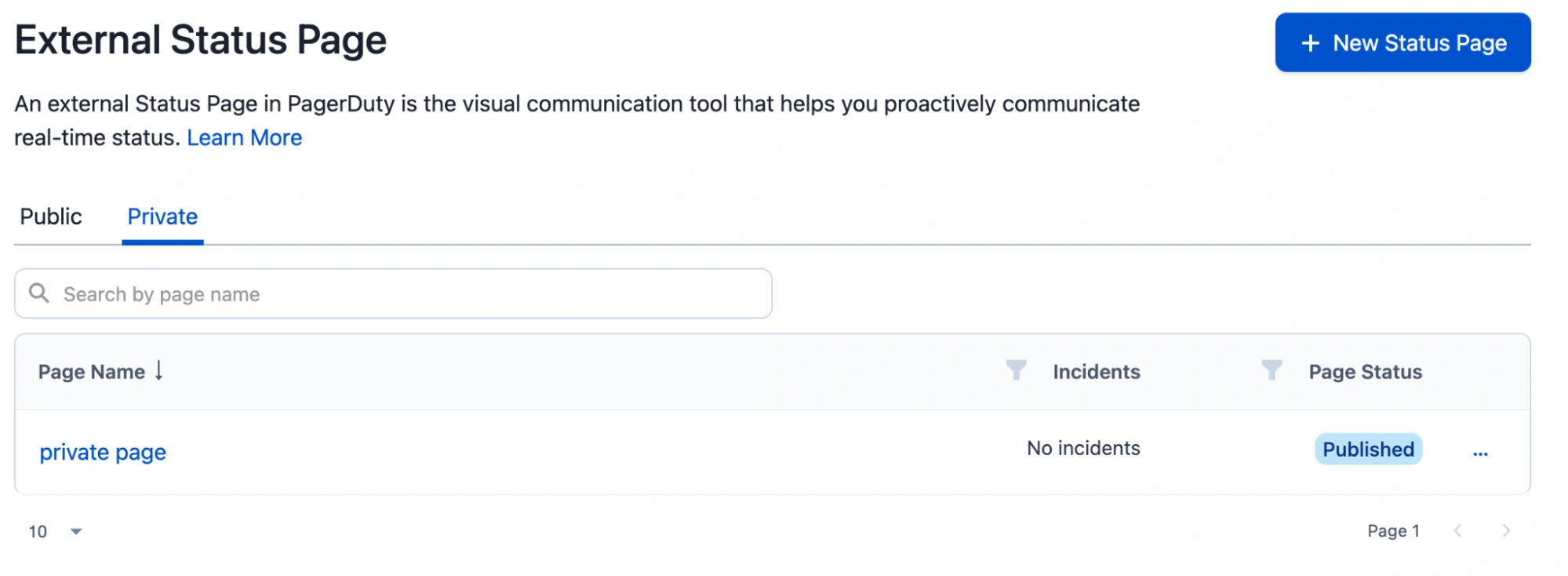
- In the PagerDuty web app, navigate to Status External Status Page, select the Private tab, and click the name of the page you want to configure.
Select Private tab
- In the left pane, select Configuration Single Sign-On tab.
- Note: If prompted to Update your SSO Configuration, click Continue to proceed. Otherwise, proceed to the next step.
- Enter the following information:
- Configuration URL (i.e., the URL on your OpenID server that ends with
/.well-known/openid-configuration) - OpenID client ID
- OpenID client secret
- Configuration URL (i.e., the URL on your OpenID server that ends with
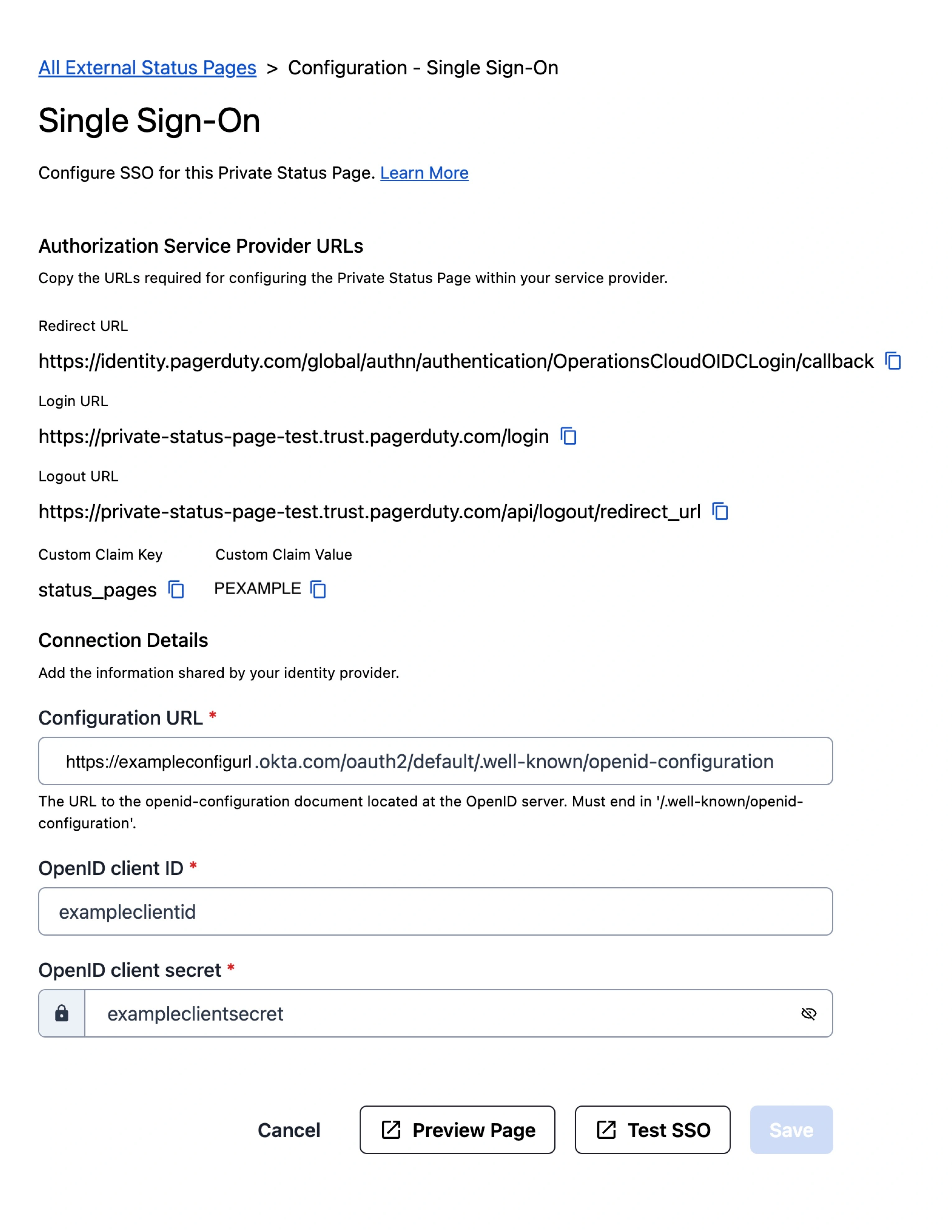
SSO configuration
- Click Test SSO to check your configuration. Resolve any reported errors and proceed to the next step.
- Note: After successfully configuring and saving your SSO settings, Test SSO may not appear in the UI the next time you visit the page.
- Take note of the Custom Claim Key and Custom Claim Value, as these will be necessary to complete the Identity Provider configuration in the next step. You'll need to create a custom claim in your IdP using this exact key name and assign the corresponding value to users who should have access to this status page.
- Click Save.
The instructions below detail how to integrate with common SSO providers. You are free, however, to integrate with the SSO provider of your choice:
Audience-Specific Status Page
Audience-Specific Status Pages enhance Private Status Pages by allowing authorized users to see customized views based on their access level. This feature is only available to users authenticated through OpenID SSO, which operates separately from PagerDuty's Single Sign-On (SSO) feature.
Audience Limit
You can add up to 100 audiences per status page.
Create an Audience-Specific Status Page
Requirements
To set up Audience-Specific Status Pages, you must first:
- Configure a Private Status Page.
- Configure SSO on the Private Status Page.
Conversion Warning
Once you convert a Private Status Page to an Audience-Specific Status Page, you will not be able to revert it. If you want all users to see the same view of the status page, you must add them to the same audience.
- After you’ve created the Private Status Page and configured SSO, click the Status Page’s name to open its settings.
- From the left menu, select the Configuration drop-down Business Services
Audiences tab. - To the right of the New Audience button, select the menu Audience Settings.
- Next, select the Default Business Services that should be visible to all users who have access to the Private Status Page.
- At the bottom of the page, enter the Group claim custom key to enable audience filtering. This is the Claim name from your SSO Provider. For example, with Okta, this is the claim name from the claim created for the Status Page Authorization Server.
- Click Save.
- Once saved, click New Audience to create a new audience view for the status page.
- Enter the following:
- Audience Name: Add a name for this audience.
- Description: Describe the purpose of this audience.
- Group Claim: Add the group claim used in your SSO provider to link groups. This must match the audience key from the SSO provider.
- Select the Business Services that should be visible to this audience, or users who sign in with credentials with this Group Claim.
- Click Create Audience to create the Audience-Specific Status Page.
Example: Configure Audience Groups in Okta
Using Okta as an example, the following is a sample flow for setting up Audiences.
Prerequisite
You must first configure Okta SSO for Private Status Pages in PagerDuty.
- In Okta, navigate to Directory Groups.
- Click Add group to create groups for the PagerDuty Status Page Audiences. Enter a Group Name and optional Description.
- Note: The names of the groups created need to match the Group Claim for each PagerDuty Audience.
- Click Save and continue adding as many groups as necessary.
- Assign users to each created group as necessary by clicking Group Name Assign people plus icon to the right of each user you’d like to assign Done in the upper right.
- Next, navigate to Security API select the Authorization Server for the Private Status Page.
- Select the Claims tab Add Claim and perform the following:
- Name: The claim name needs to match the Group Claim custom key on the Audience setting page in PagerDuty.
- Included in token type: Select ID Token = Always
- Value Type: Select Groups
- Filter: Matches regex =
.*- This is to match any groups available
- Disable claim: Leave unchecked
- Include in: Any scope
- Click Create. You should now be able to see the audiences in the token under the Token Preview tab Preview Token.
Okta
Create the Application
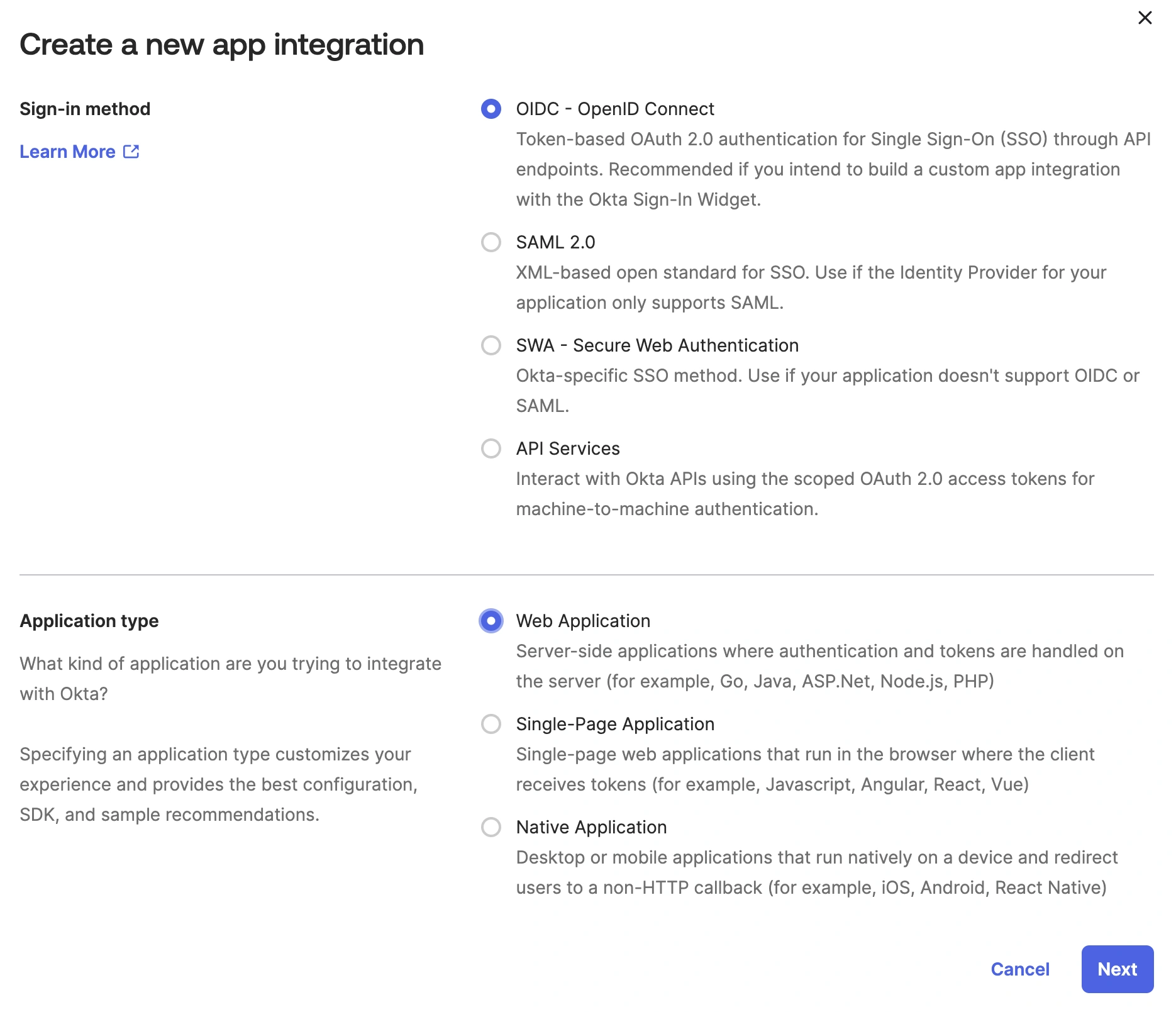
- Go to Applications Create App Integration.
- For Sign-in method, select OIDC - OpenID Connect, and for Application type, select Web Application. Click Next.
Create a new app integration
- Under Application, enter a name for the application.
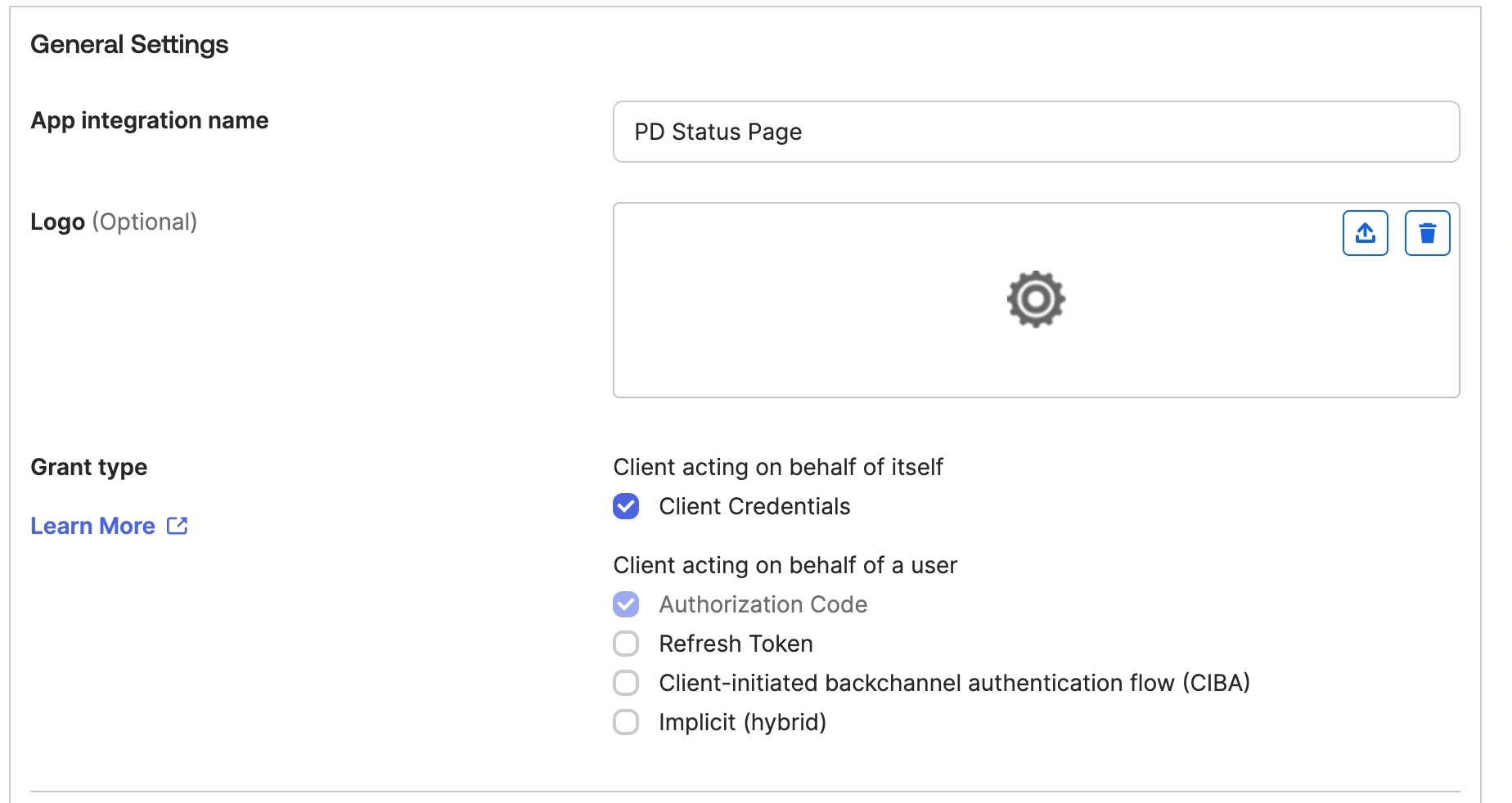
General settings
- Copy the Redirect URL from the SSO configuration in PagerDuty and paste it into the Sign-in redirect URI. Do the same for the Login URL and the Sign-out redirect URIs.
- Select how you would like to assign the application, and click Save.
- On the next page, copy the client ID and client secret, and paste it into the OpenID client ID and OpenID client Secret fields on the PagerDuty SSO configuration page.
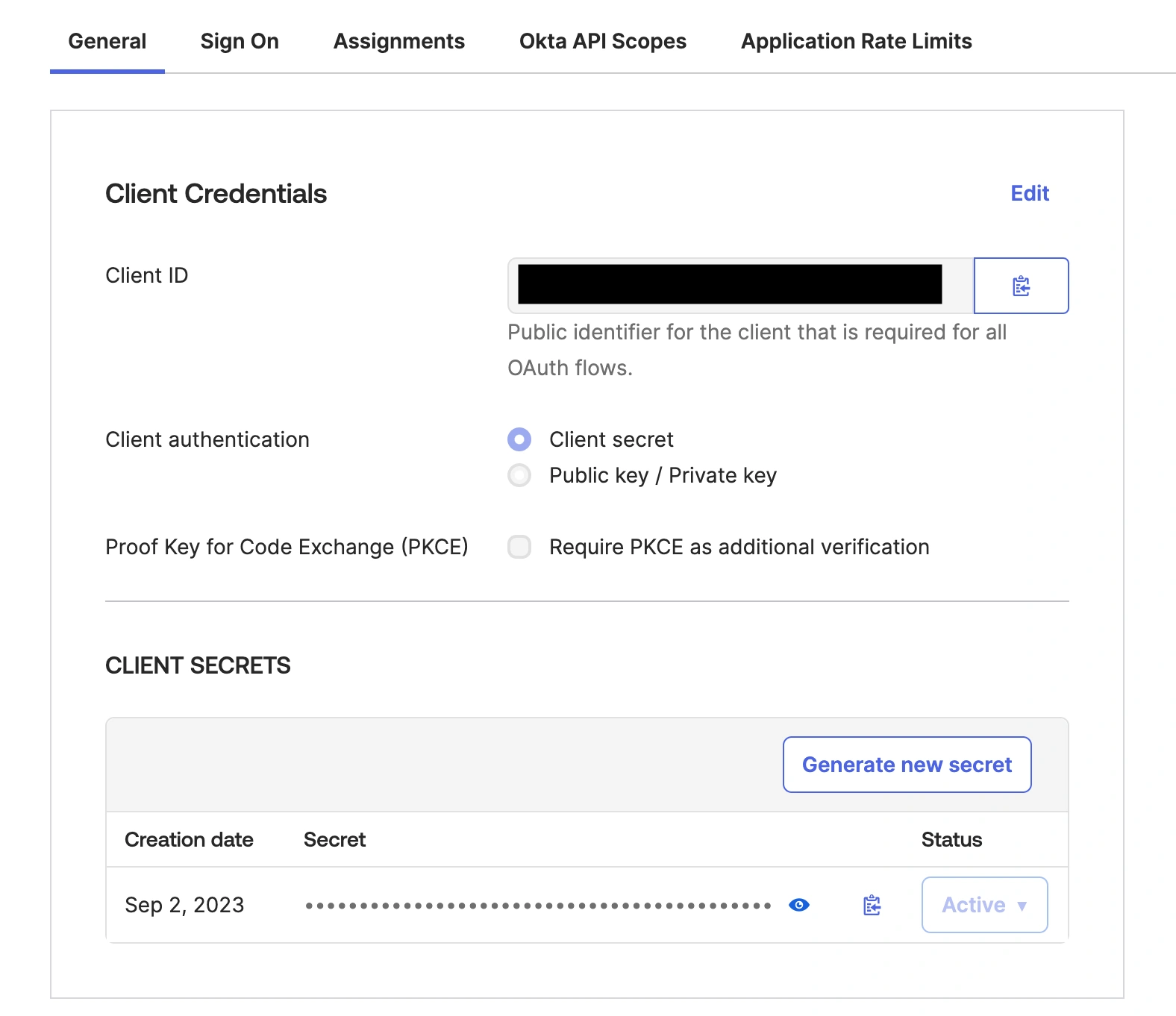
Client credentials
- Go to Security API and select the Authorization Server you want to connect.
- Copy the Metadata URI and paste it into the Configuration URL field in the PagerDuty SSO configuration page.
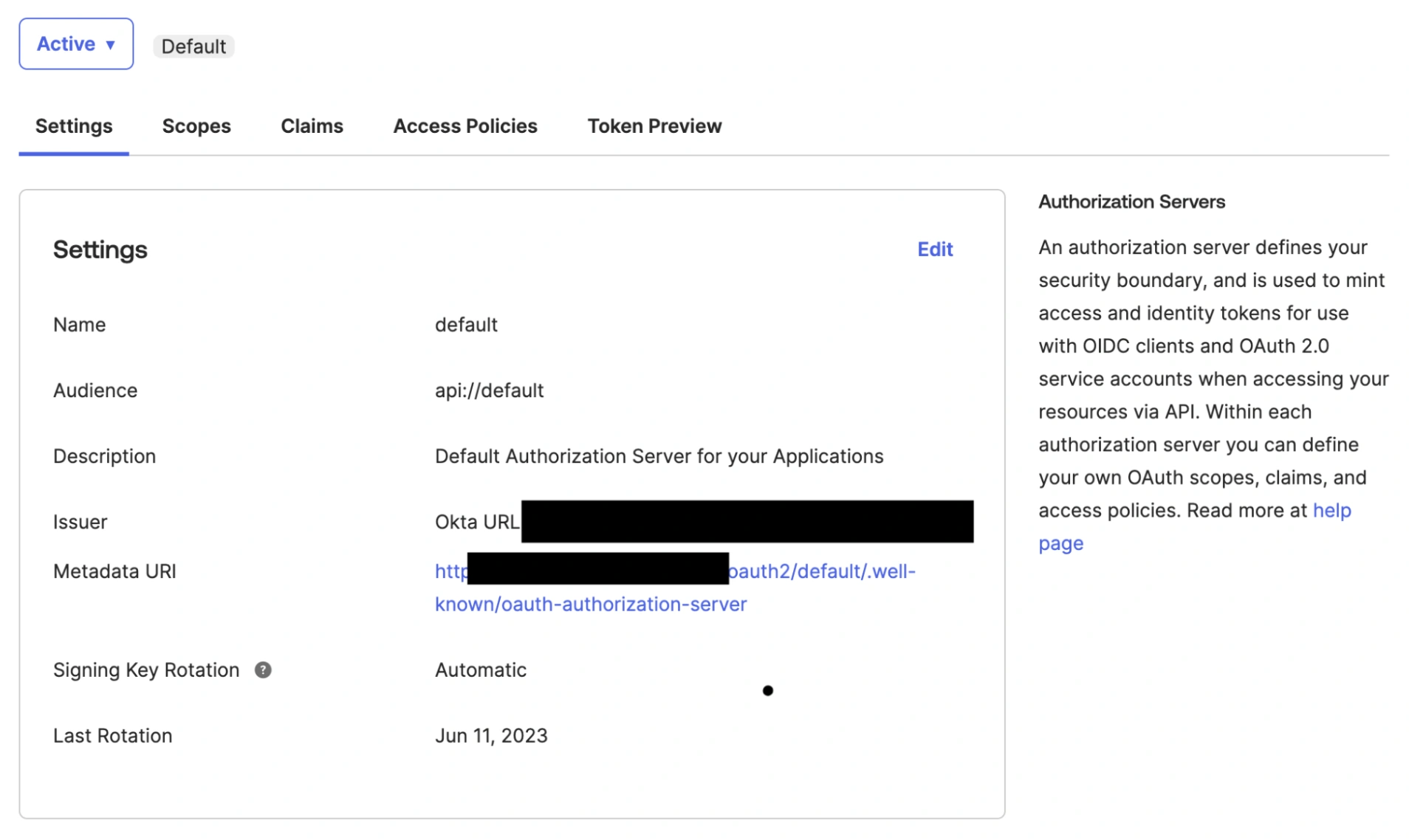
Metadata URI
- Replace the end of the URL (
oauth-authorization-server) withopenid-configuration. The URL in PagerDuty must end with/.well-known/openid-configuration. - Save the SSO configuration.
Profile Mapping and Custom Claims
- Go to Directory Profile Editor and select your application.
- Click Add Attribute. For the Data type, select string. Enter a Display name. For the variable name enter
pd_status_pages. Select Greater than for Attribute length, with a value of 0. Select Yes for Attribute required and click Save.
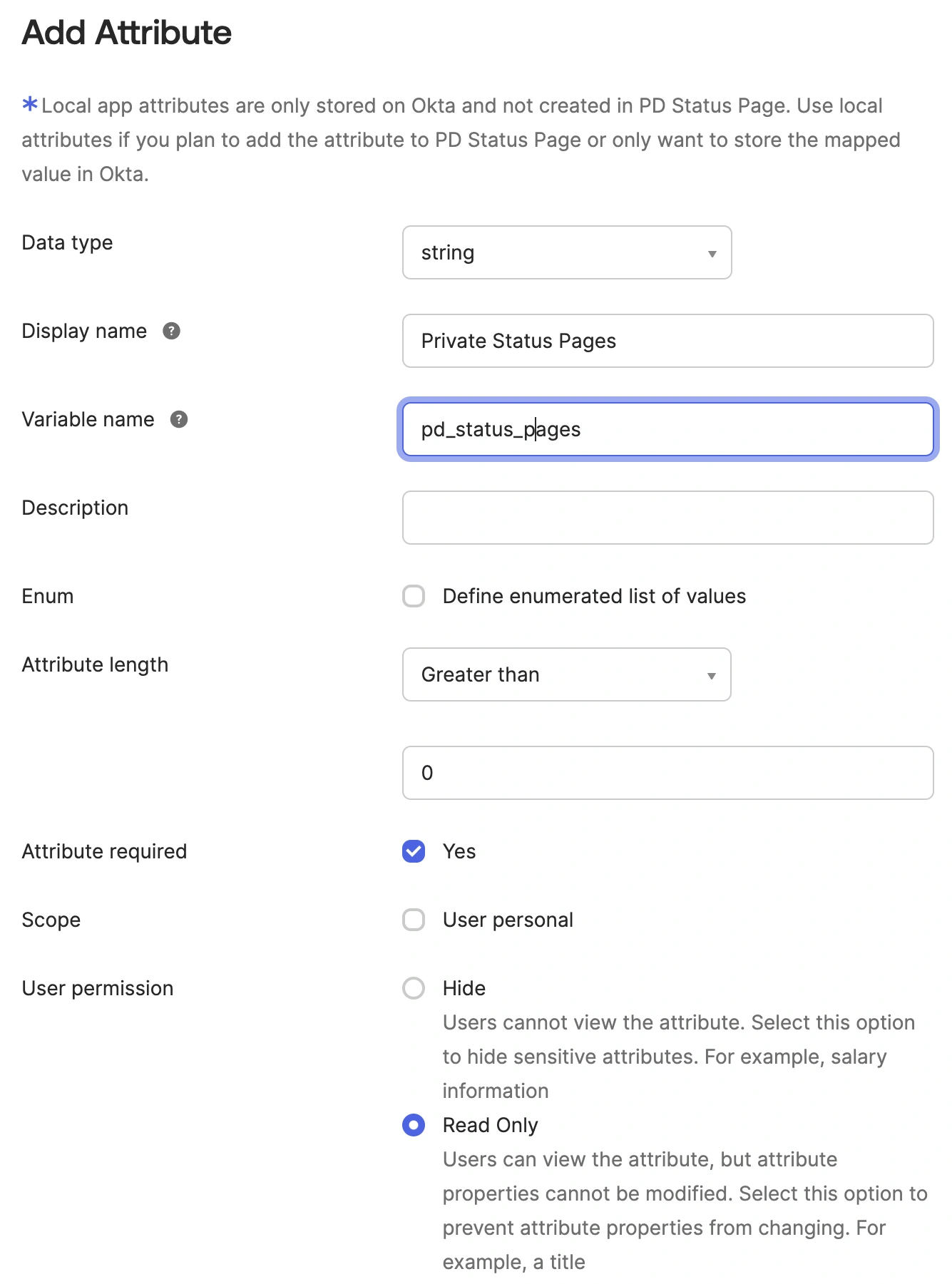
Add attribute
- Click Mappings, and find
pd_status_pages. Ensure that Apply mapping on user create and update is selected (i.e., it shows a green arrow). Enter the custom claim value from the PagerDuty SSO configuration page, surrounded by single quotes, and click Save Mappings.
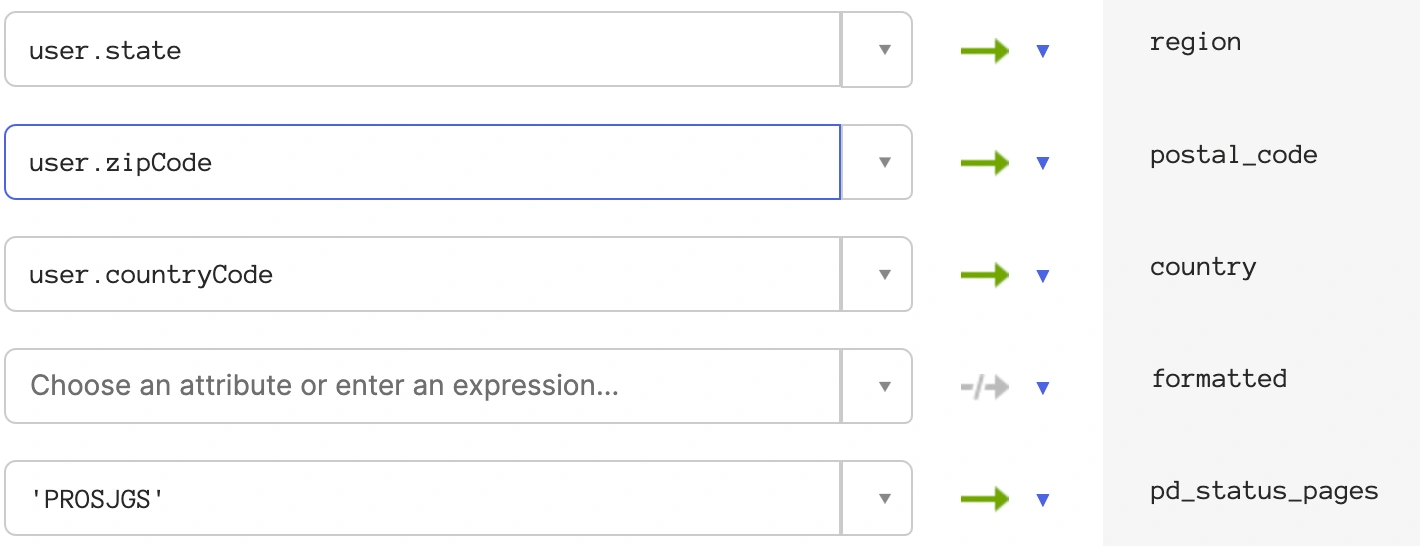
Custom claim value
- Go to Security API and select the authorization server you will be using. Then select the Claims tab and click Add Claim.
- In the Name field, enter the name found under the Custom Claim Key on the PagerDuty SSO configuration page. Select ID Token as Always. Under Value, enter
appuser.pd_status_pages.
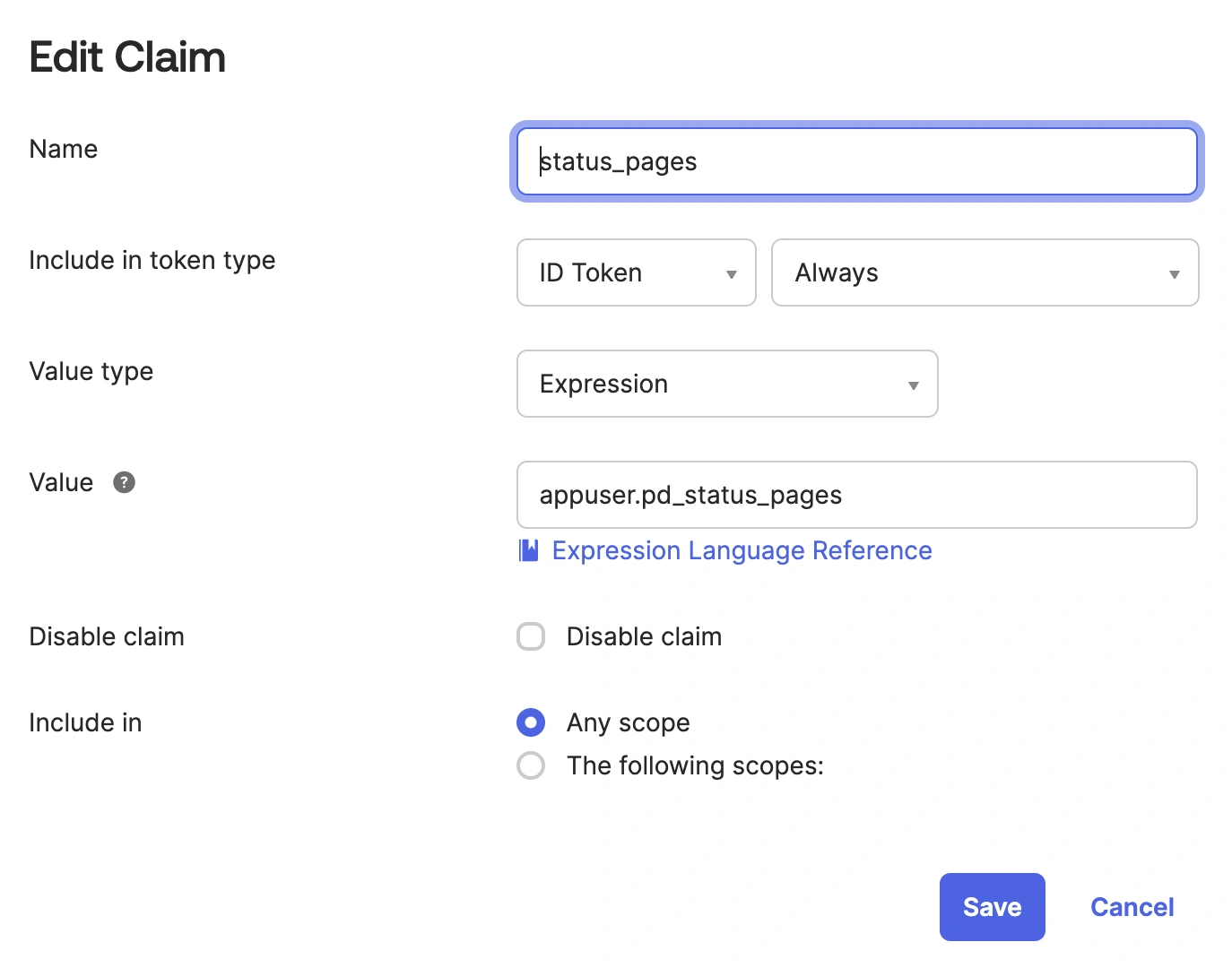
Edit claim
Data Requirement
The name of the claim must match the Custom Claim Key name.
Azure AD / Entra ID
Create the Application
- In the Microsoft Entra Admin Center, navigate to App Registrations New Registration.
- Enter a name for the app and the Redirect URI from the PagerDuty SSO Configuration page.
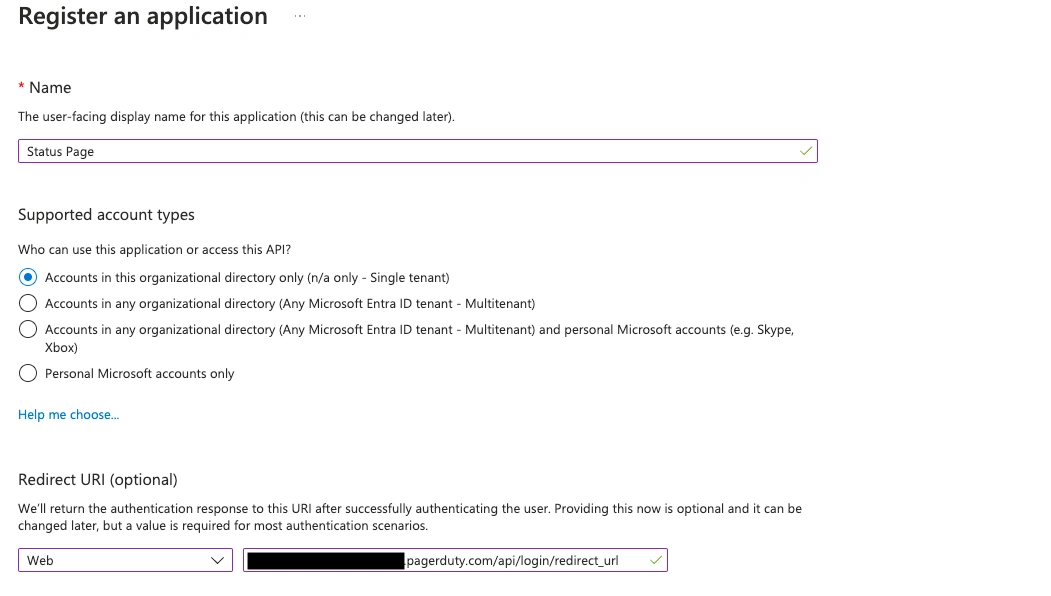
Register an application
- Find the newly created app under App Registrations and select it. Then, click Add a certificate or secret to create a client secret. On the next screen, click New Client Secret.

Add a certificate or secret
- Copy newly created client secret and paste it into the PagerDuty SSO configuration page. Then go back to the previous page and copy and paste the Application (i.e., client) ID.
Note: you will be presented with an array of values associated with your client secret.- Typically the values will include the following fields: Description, Expires, Value, Secret ID.
- Look for the secret's Value field.
- Note: Please do not use the data in the Secret's Secret ID field, which is UUID and not intended for the secure use.
- Go back to the previous screen and click Authentication. Under Front-channel logout URL, add the logout URL from the PagerDuty SSO Configuration page and Save.
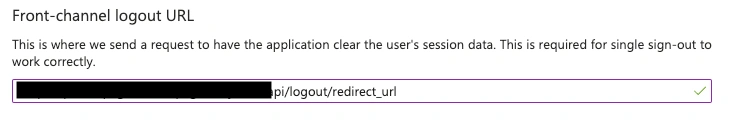
Redirect URL
- In the same menu where Authentication was found, select Manage Branding and Properties. In the Home page URL field, enter the login URL from the PagerDuty SSO Configuration page and click Save.
Home page URL
- Go back to the created application (as in step 3), and click on Endpoints. Locate the OpenID Connect metadata document URL and copy it and paste it into the Configuration URL on the PagerDuty SSO Configuration page.
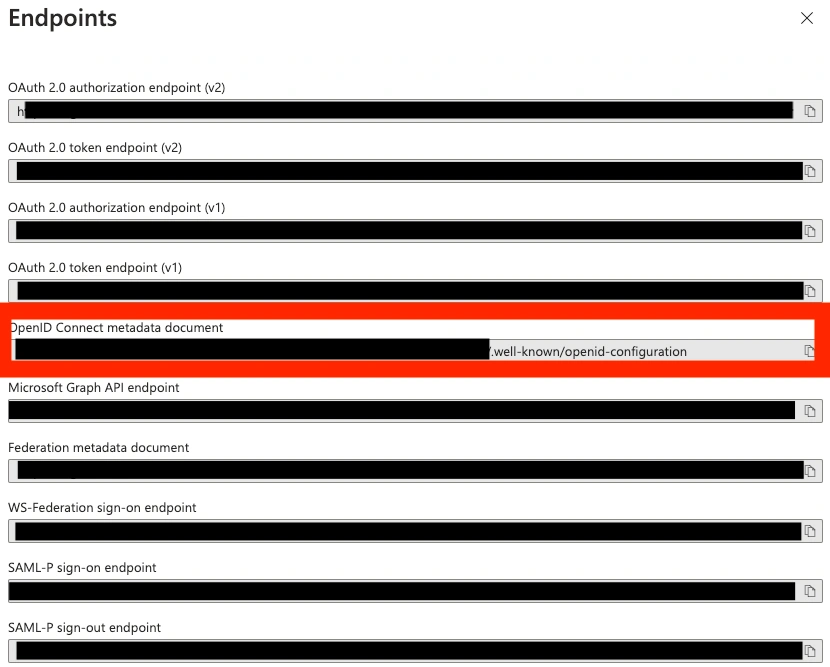
OpenID Connect metadata document
Profile Mapping and Custom Claims
- On your app page (from app registration), select Manage App roles.
App roles
- Click Create Role, and enter the custom claim key and custom claim value found on the PagerDuty SSO configuration page. Click Apply.
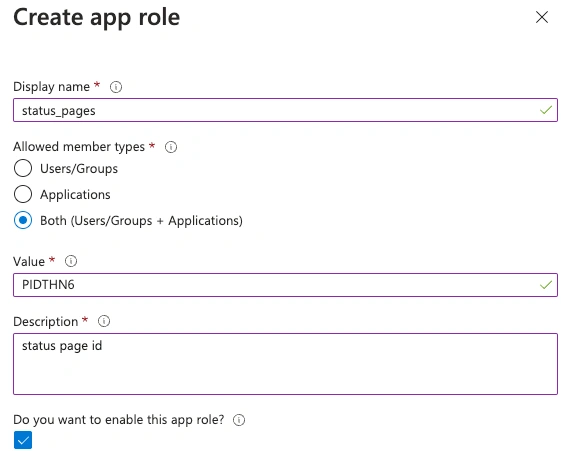
Create app role
- Under Manage, select Manifest. In the JSON representation, update
acceptMappedClaimstotrueand save. - Go to Applications Enterprise Applications, select the application, and go to Single Sign-On. Click Edit next to Attributes & Claims.
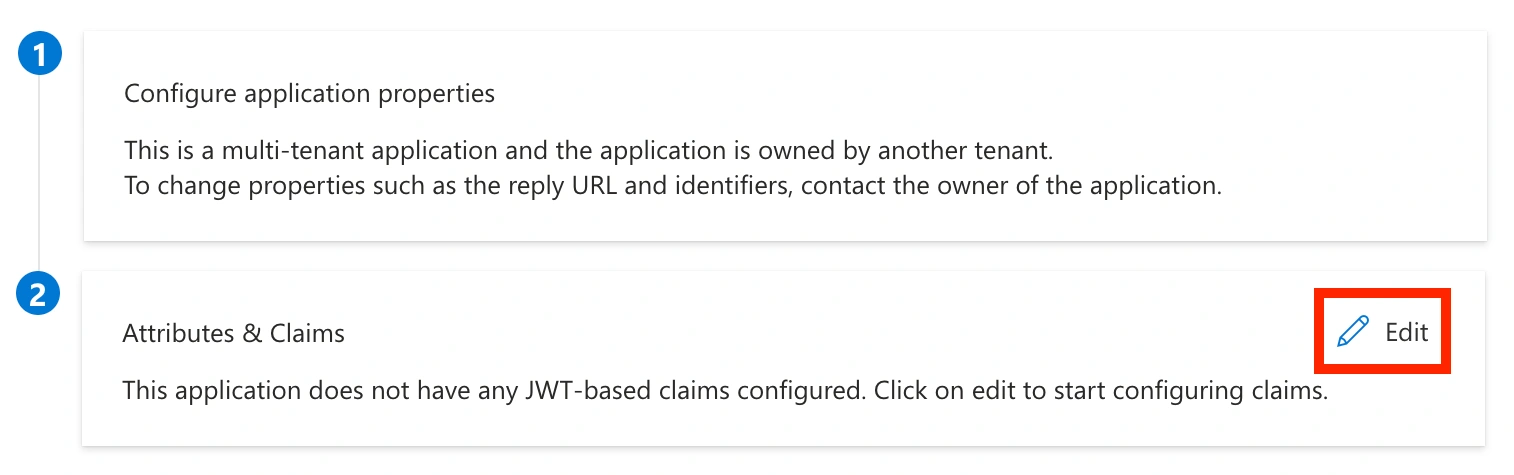
Attributes and Claims
- Click Add New Claim. Enter the custom claim key (
status_pages) for the name. Under Source, select Attribute, and under Source attribute, enteruser.assignedroles. Click Save.
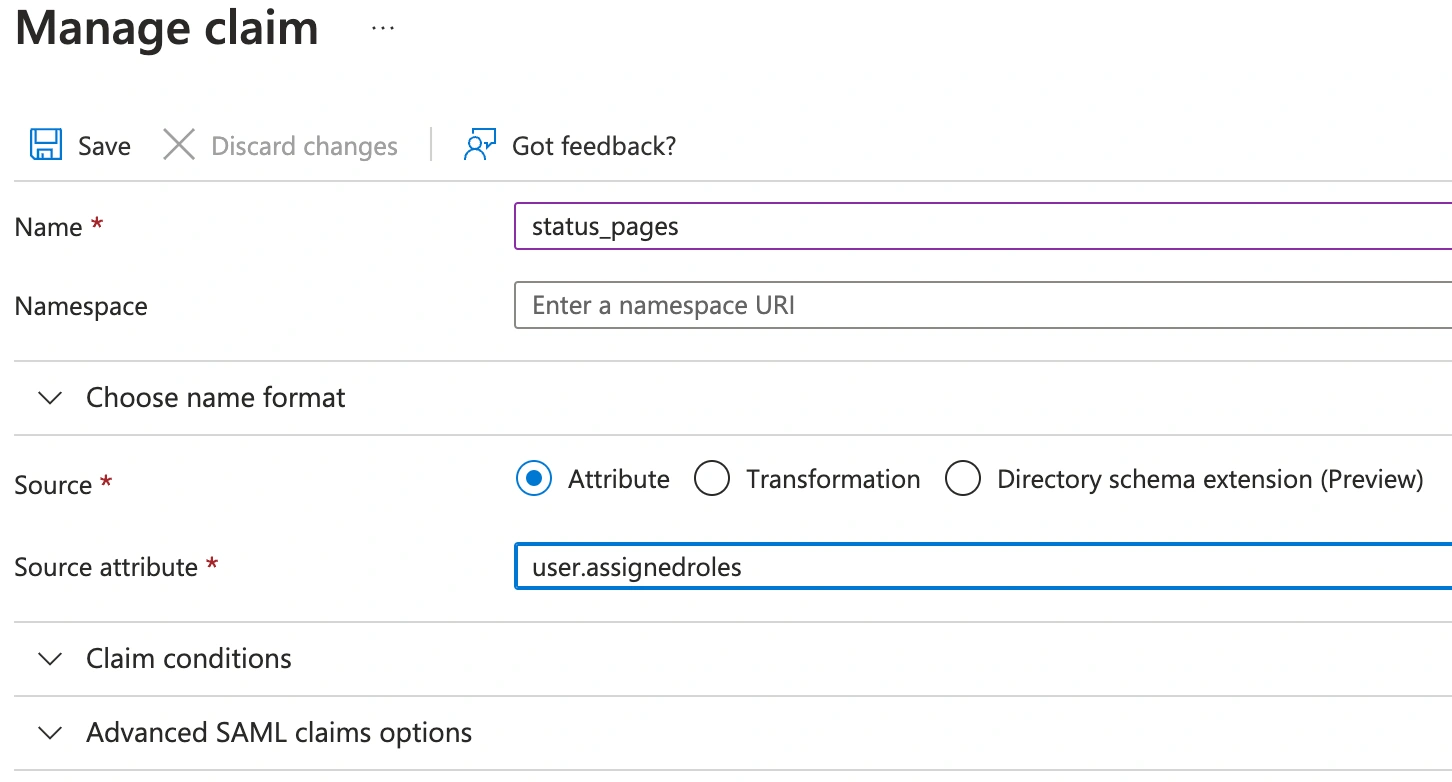
Manage claim
- Go to Applications Enterprise Applications, select the application, and go to Users and groups. Click Add user/group. Select the users who should have access to the private status page, then select the
status_pagesrole. Click Assign.
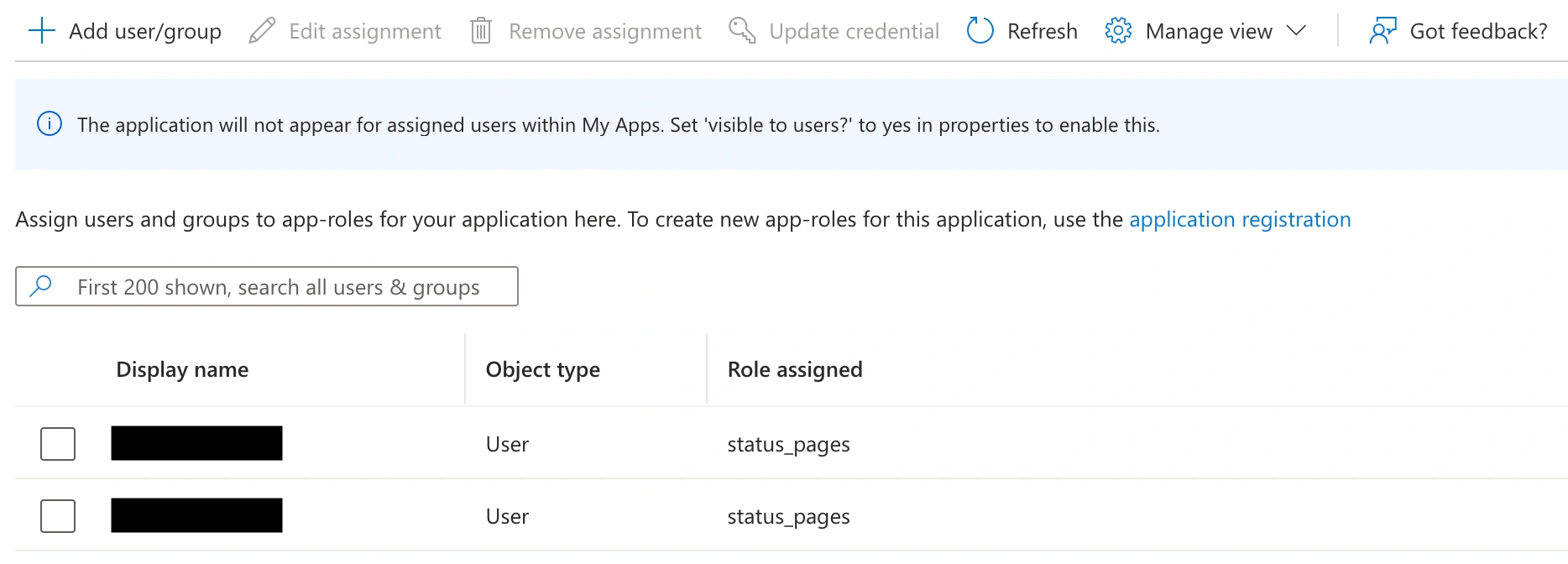
Assign app role
Salesforce
Create the Application
-
Ensure that the Identity Provider is enabled in Salesforce. In the Setup view go to Settings Identity Identity Provider, and click Enable Identity Provider.
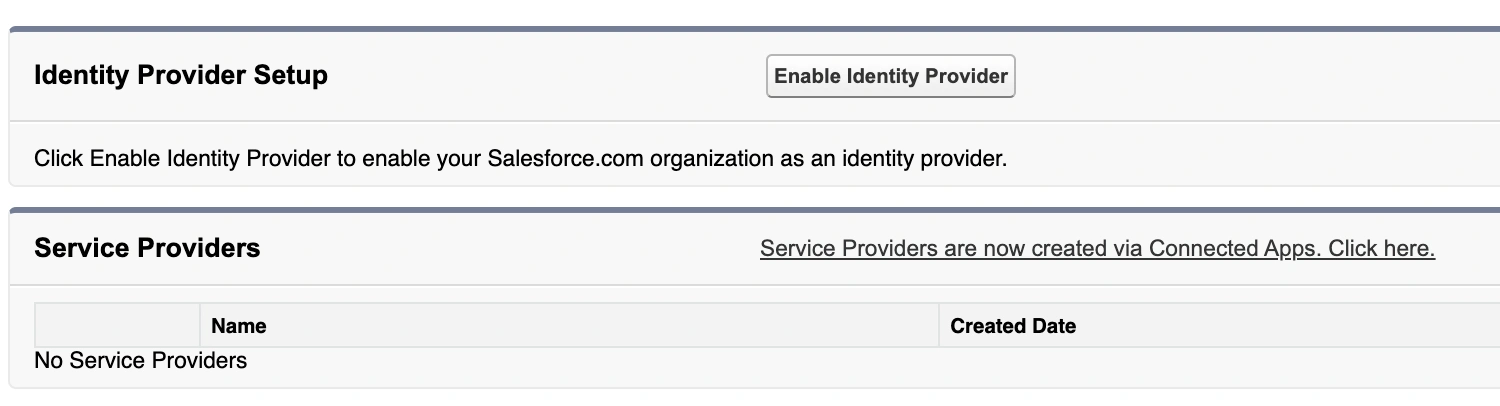
Enable identity provider
-
Go to Settings Identity OAuth and OpenID Connect Settings and ensure that the Allow Authorization Code and Credentials Flows option is enabled.
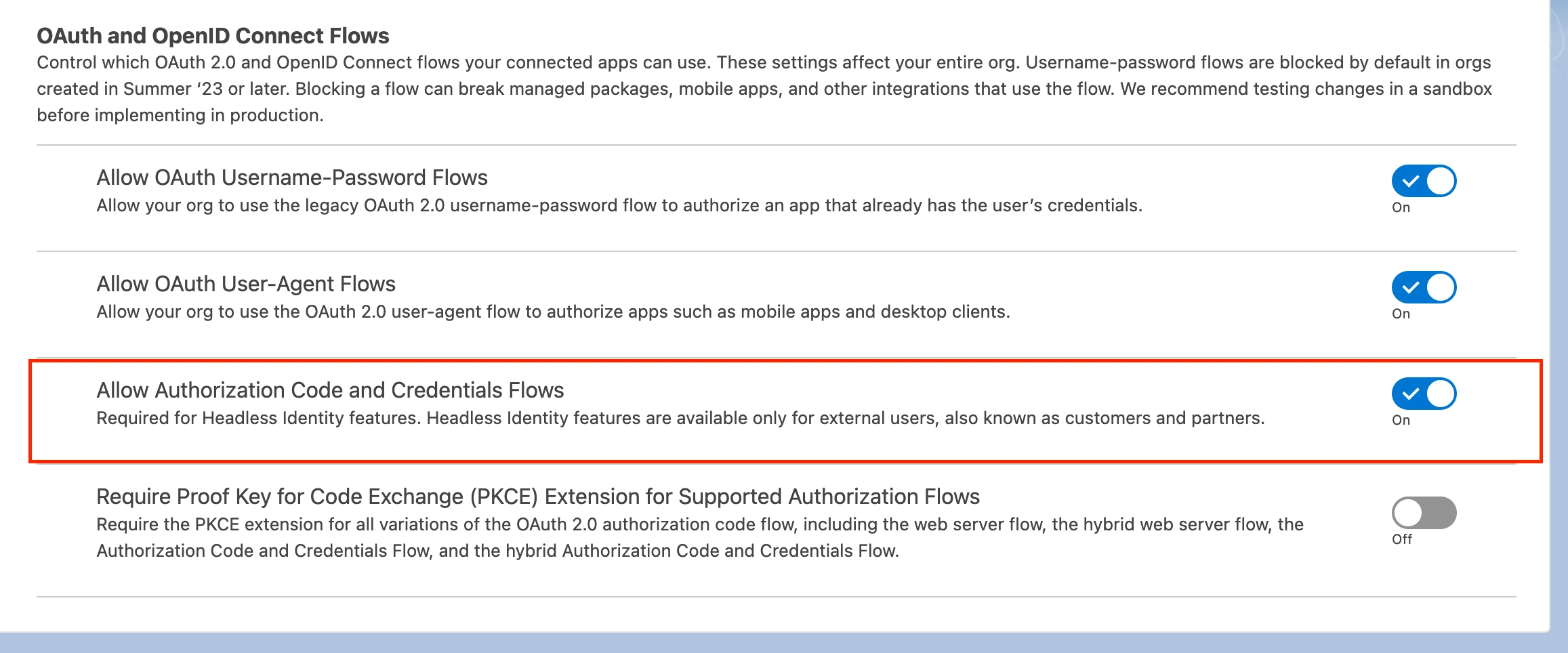
Allow Authorization Code and Credentials Flows
-
Go to Platform Tools Apps App Manager and click New Connected App.
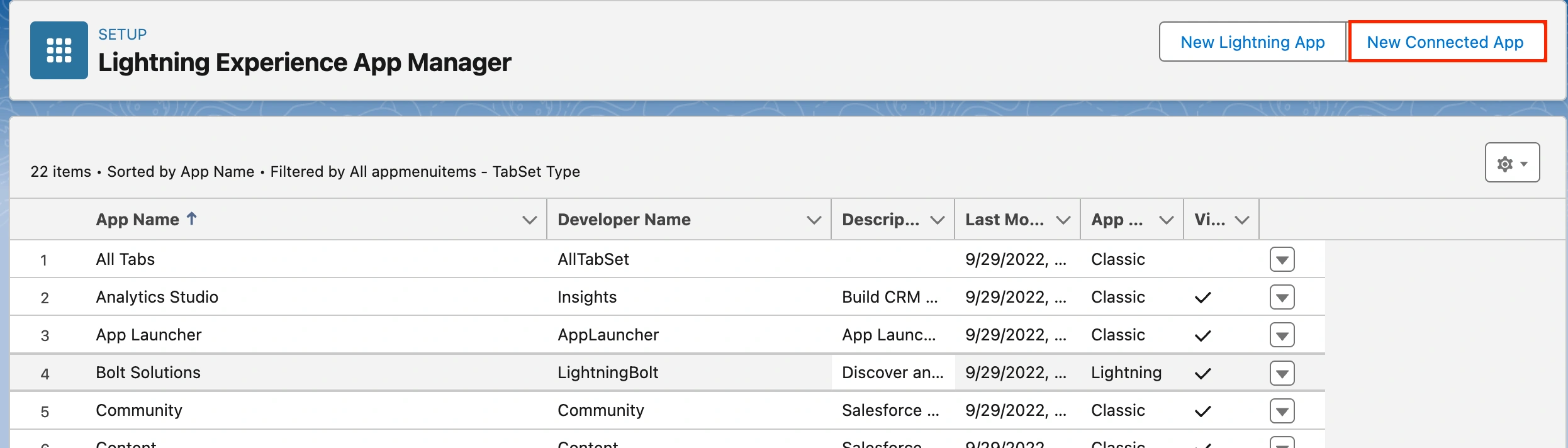
New connected app
-
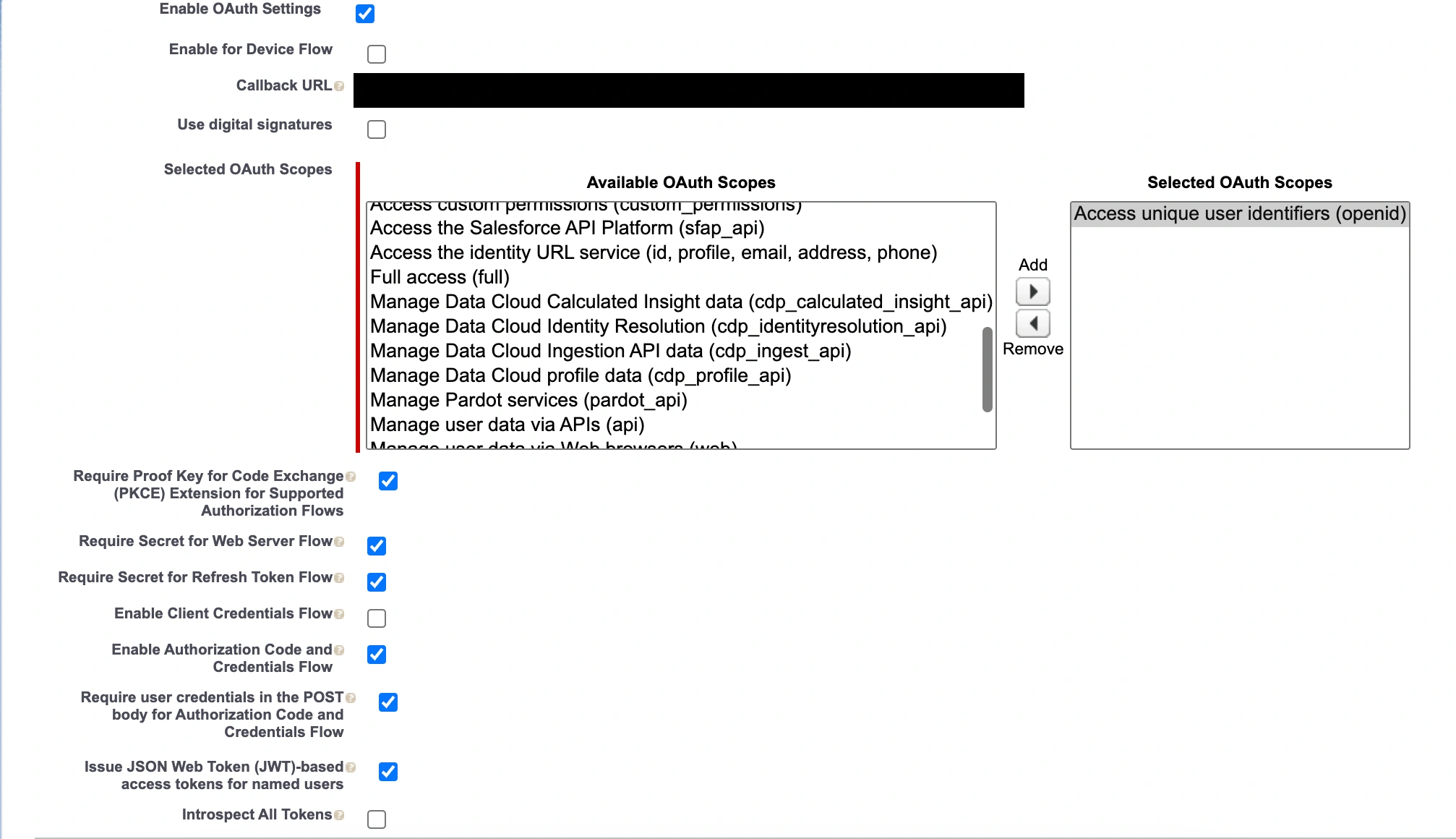
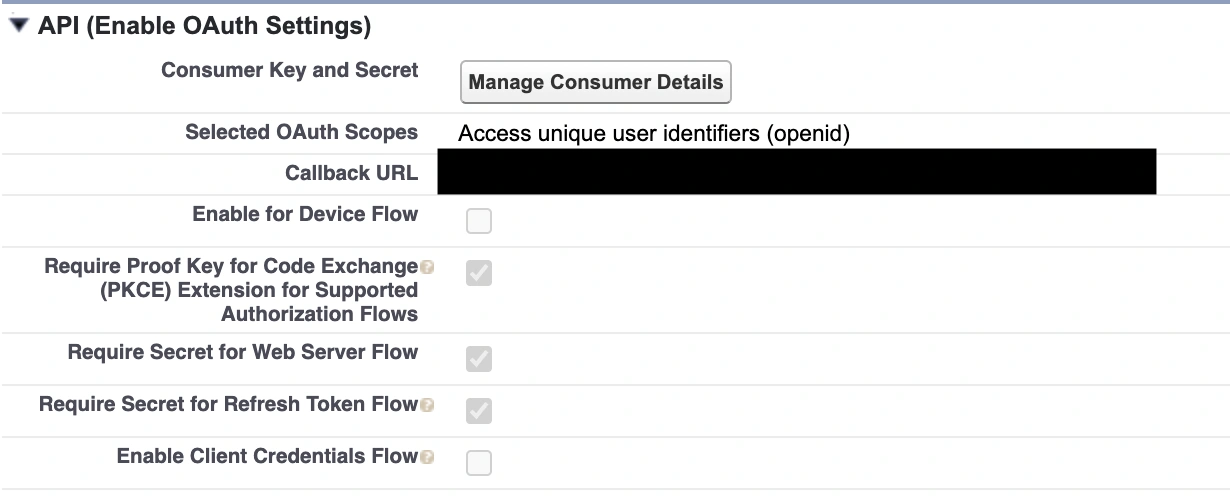
Enter basic information, then enable OAuth settings and populate the following fields, and save:
-
Callback URL: use the redirect URL from your PagerDuty Private Page
-
Selected OAuth Scopes: Add Access unique user identifiers (openid)
-
Enable Authorization Code and Credentials Flow: Enable
-
Require user credentials in the POST body for Authorization Code and Credentials Flow: Enable
-
Require Secret for Web Server Flow: Enable (optional)
-
Issue JSON Web Token (JWT)-based access tokens for named users: Enable
-
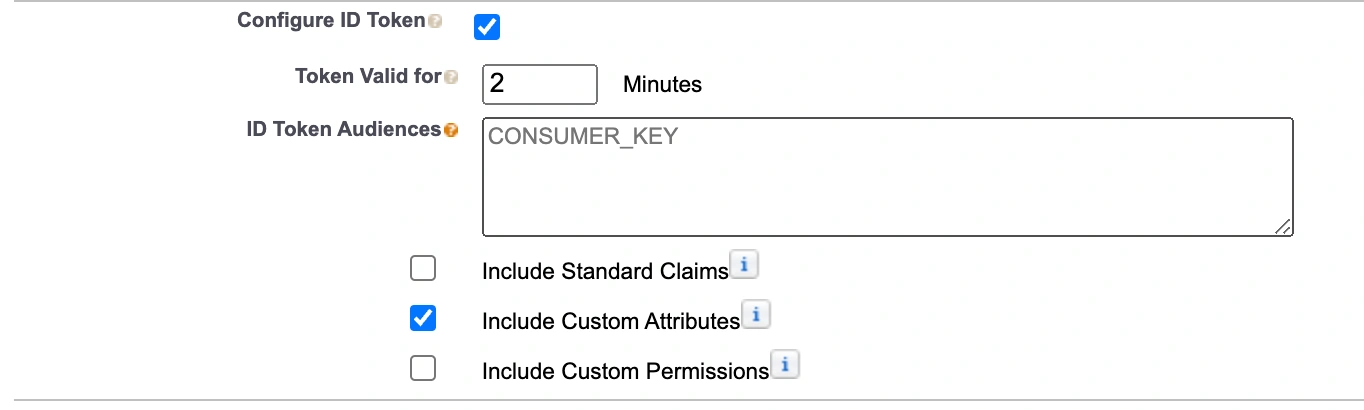
Configure ID Token: Enable
-
Include Custom Attributes: Enable
-
-
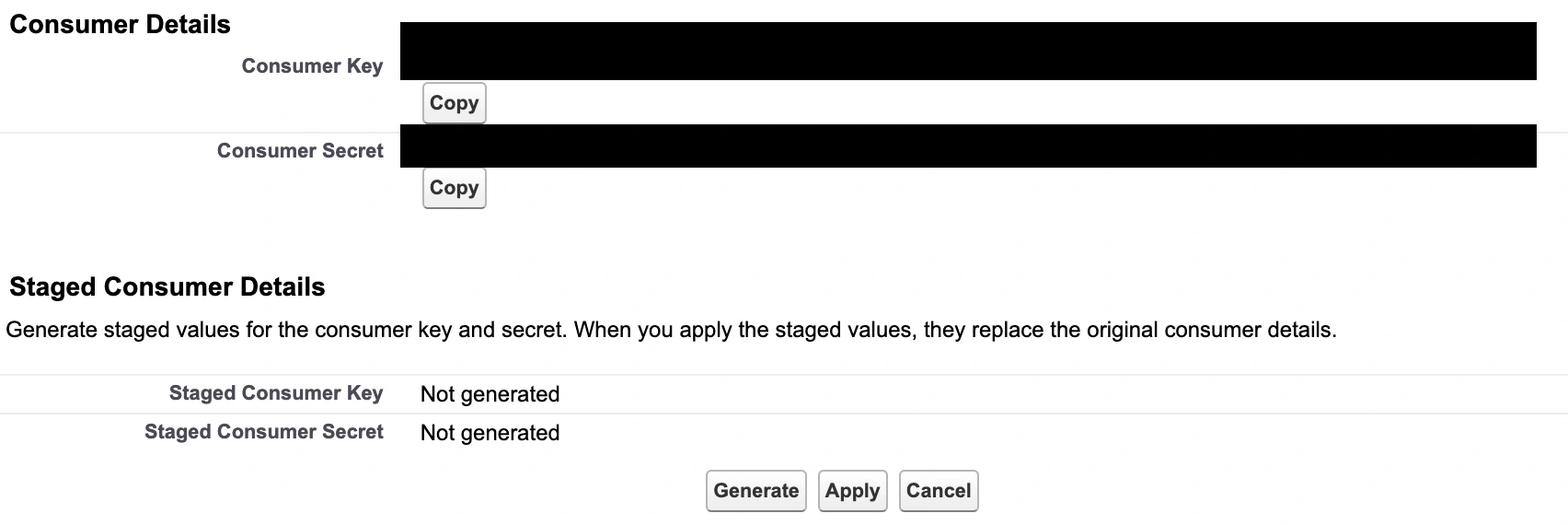
After saving, click on Manage Consumer Details to get the Consumer Key and Consumer Secret.
-
On your PagerDuty private page Single Sign-On Settings, populate the following fields and save:
- Configuration URL:
https\://{{your-workspace-domain}}.my.salesforce.com/.well-known/openid-configuration - OpenID client ID:
{{Consumer Key}} - OpenID client secret:
{{Consumer Secret}}
- Configuration URL:
Profile Mapping and Custom Claims
-
Back in Salesforce, grant permissions to the groups that you want to be able to access the page (if users are not self-authorizing). To do this, go to Apps Connected Apps Manage Connected Apps and click on Manage Permissions under the Permission Sets field.
Permission sets
-
Finally, to add the status page ID, go back to the previous view (i.e., Manage Connected Apps) and click New next to Custom Attributes.
-
Paste the Custom Claim Key and Custom Claim Value from the PagerDuty SSO settings, into the Attribute key and Attribute value fields.
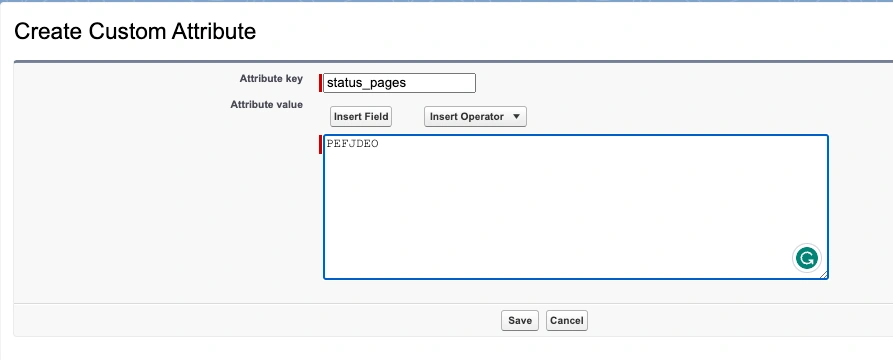
Create custom attribute
Ping Identity
Create the Application
-
Go to Applications, and click to add a new application.
Add application
-
Enter an application name, select an application type, and click Save.
Application settings
-
Click on the Configuration tab and the URLs dropdown.
-
Copy the OIDC Discovery Endpoint, the Client ID, and the Client Secret, and paste these values into the PagerDuty private page Single Sign-On Settings.
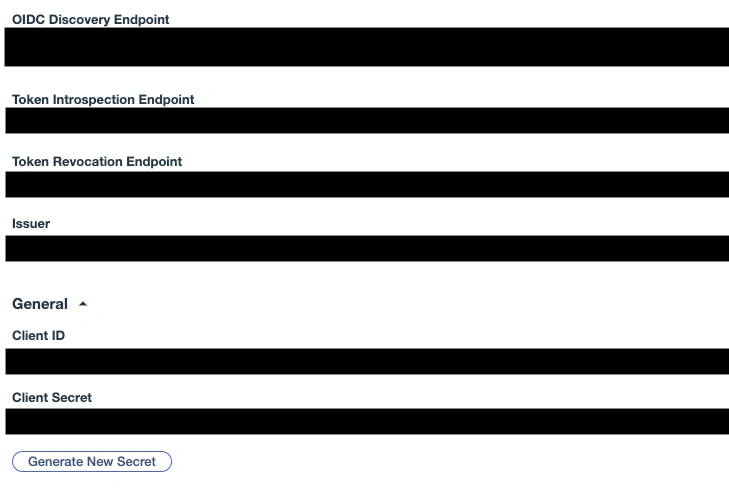
-
Edit the configuration by clicking the pencil button in the top right corner, update the following fields, and save:
- Client Credentials: Enable
- Redirect URIs: the redirect URL from the PagerDuty Single Sign-On page
- Token Endpoint Authentication Method: Client Secret Post
- Initiate Login URI: Login URL from the PagerDuty Single Sign-On page
- Signoff URLs: Logout URL from the PagerDuty Single Sign-On page
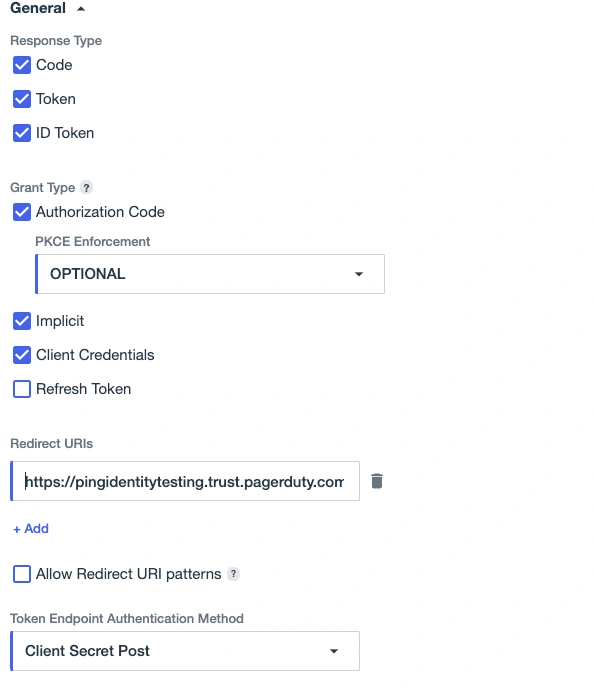
General settings
-
In the Resources tab, check that the openid scope is available.
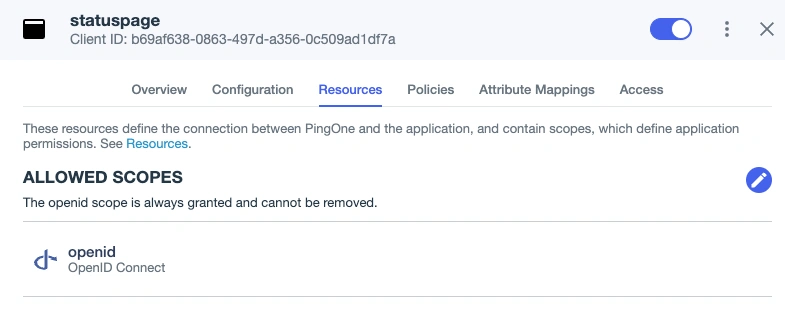
Allow openid
Profile Mapping and Custom Claims
-
Go to Directory User Attributes and click to add a new attribute.
-
Select Declared, enter a name for the attribute and save it.
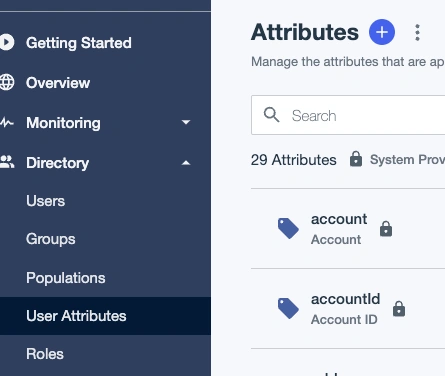
Add attribute
-
Go to Users, edit any users you want to grant access, and click Add next to Custom Attributes. Enter the custom claim ID value found on the Single Sign-On page.
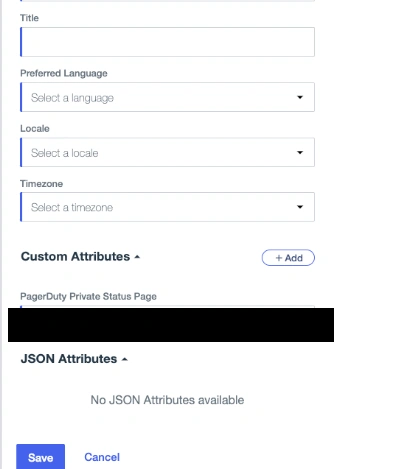
Custom attributes
-
Go to Applications Resources, find the openid resource that is being used, and select it.
-
Go to the Attributes tab and click to add a new attribute.
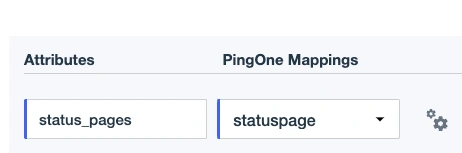
Attributes
-
Enter the Custom Claim Key from the Single Sign-On page and select the attribute that you created in steps 1–3.
Remove Users from a Private Status Page
Removing a user's access through your SSO provider alone will not automatically remove them as a subscriber to a Private Status Page in PagerDuty as well. They may continue to receive status update until you have taken the following steps:
- Remove the user's access in your SSO provider. Please see your SSO provider's documentation for specific instructions.
- In the PagerDuty web app, navigate to Status External Status Page.
- Select the desired status page's name.
- In the left panel, select Subscribers.
- Select the appropriate tab (i.e., Email, Slack or Webhook), and optionally enter a search term to find the desired user.
- On the right of the user's row, select Delete.
- In the confirmation modal, click Yes, delete.
Updated 4 months ago
