Advanced Permissions
Configure granular user access with Advanced Permissions
Administrators can use Advanced Permissions to specify a user’s Team role, as well as their level of access to incidents and configuration objects such as services, escalation policies and schedules. Advanced permissions provide granular access control, allowing you to fully customize permissions according to your organization’s needs.
Availability
- Advanced Permissions are available to customers on the following pricing plans: Professional, Business, Digital Operations (legacy) and Enterprise for Incident Management. Please contact our Sales Team if you would like to upgrade to a plan with this feature.
- If you are already on a Professional, Business, Digital Operations (legacy) or Enterprise for Incident Management, but do not yet have Advanced Permissions enabled, contact PagerDuty Support to request enablement.
Benefits of Advanced Permissions
- Increased Control and Security: Teams can determine who is allowed to respond to incidents and manage their Team's configuration. Individual users can also create and manage API user keys/tokens.
- Prevent Human Error: By empowering Teams to control access to their incidents and configuration, accidents that might interfere with a Team’s process can be mitigated.
- Limit the Visibility of Sensitive Information: Teams can be set to private if their incidents or configuration contain sensitive information.
Free Accounts
PagerDuty accounts with a Free pricing plan handle user permissions in a different way. Please read User Roles if your account is on a Free pricing plan.
Role Types
With Advanced Permissions, there are three different types of roles:
Each role is unique and dictates what a user has access to.
Base Roles
All users in an account have a base role, and when you add a new user, they must be assigned one. A user’s base role indicates the default level of access they have to incidents and configuration objects across the entire account. To find your own base role, navigate to User Icon My Profile Permissions & Teams tab.
Base roles can either be flexible or fixed:
- Fixed Base Roles: A fixed base role is one that you cannot grant more or fewer permissions via a Team role or an object role.
- Flexible Base Roles: A flexible base role is one that you can grant more or fewer permissions via a Team role or an object role.
| Role Name | Role Type | Description |
|---|---|---|
| Account Owner | Fixed | Full access to create, update, and delete objects, including other users' permissions. Account Owners can also access the Subscription and Account Settings pages. There can only be one Account Owner user per account. |
| Global Admin | Fixed | Full access to create, update, and delete objects, including user permissions. Global Admins can also purchase additional user licenses via the Users page. |
| Manager | Flexible | Full access to create, update, and delete objects and administer their configuration settings. At the Account Owner or Global Admins' discretion, they may give Managers lower access levels for specific objects. |
| Responder | Flexible | Can take action on incidents, create incidents for any Team, and create schedule overrides. |
| Observer | Flexible | Can view objects, but cannot make modifications. If you assign an Observer to an incident, they will temporarily have Responder access to that incident only, and can respond to the incident or reassign it. Observers can trigger incidents from the PagerDuty Slack app. |
| Full Stakeholder | Fixed | Can view objects, but cannot make modifications. You cannot assign Full Stakeholders to incidents, nor can they respond to them. For more information, please read our section on Full Stakeholders. |
| Limited Stakeholder | Fixed | Can only view and subscribe to internal status pages, and they can view and edit their user profile. Limited Stakeholders cannot view any other parts of PagerDuty. For more information, please read our section on Limited Stakeholders. |
| Restricted Access | Flexible | You must give Restricted Access users a specific Team or object role before they can view objects in the account. |
Base Role Actions
Below are two general lists of actions each base role can take divided by flexible and fixed roles. For flexible base roles, the table indicates the level of access each role has by default on an account before an administrator configures more or fewer permissions via a Team or object role.
Feature Permissions
The lists below are not exhaustive. You can check the Required User Permissions callouts on each feature's article to find out what permissions are required.
Flexible Base Roles
| Restricted access | Observer | Responder | Manager | |
|---|---|---|---|---|
| Subscribe to incidents | ✓ | ✓ | ✓ | ✓ |
| Create/delete personal REST API access keys/tokens matching permissions level | ✓ | ✓ | ✓ | ✓ |
| Respond to their assigned incidents | ✓ | ✓ | ✓ | ✓ |
| Addable to schedules and escalation policies | ✓ | ✓ | ✓ | ✓ |
| View all public Teams, services, schedules, escalation policies, analytics and postmortems across the entire account | ✓ | ✓ | ✓ | View alerts from services that they have access to in the Alerts table. (Permission to view services may be restricted by Team and/or Object roles.) | ✓ | ✓ | ✓ |
| Trigger and respond to incidents for any public Team | ✓ | ✓ | ||
| Create/delete overrides on any schedule | ✓ | ✓ | ||
| Create custom incident actions | ✓ | |||
| Add/edit/delete any: ∙ On-call schedules ∙ Schedule overrides ∙ Escalation policies ∙ Services ∙ Maintenance windows ∙ Teams ∙ Incident Workflows ∙ Business Services ∙ Business Services on incidents |
✓ | |||
| Edit and update webhooks and extensions | ✓ | |||
| View/edit/delete all private Teams and their services, schedules, and escalation policies across the entire account | ||||
| Create/delete global API key/token | ||||
| ∙ Manage users ∙ Add new users ∙ Delete users ∙ Edit users’ profiles and passwords ∙ Configure users' base roles, Team roles, and object roles |
||||
|
∙ Redact Incidents ∙ Administer the account ∙ Change the account owner ∙ Edit billing information ∙ Add/edit/delete single sign on (SSO) properties ∙ Delete the account ∙ Change pricing plans |
Fixed Base Roles
| Limited Stakeholder | Full Stakeholder | Global Admin | Account Owner | |
|---|---|---|---|---|
|
∙Only has access to internal status pages and their own user profile ∙ Cannot view any other account objects |
✓ | |||
| Subscribe to incidents | ✓* | ✓* | ✓ | ✓ |
| Create/delete personal REST API access keys/tokens matching permissions level | ✓ | ✓ | ✓ | |
| Respond to their assigned incidents | ✓ | ✓ | ||
| Addable to schedules and escalation policies | ✓ | ✓ | ||
| View all public Teams, services, schedules, escalation policies, analytics and postmortems across the entire account | ✓ | ✓ | ✓ | View alerts from services that they have access to in the Alerts table. (Permission to view services may be restricted by Team and/or Object roles.) | ✓ | ✓ | ✓ |
| Trigger and respond to incidents for any Team | ✓ | ✓ | ||
| Create/delete overrides on any schedule | ✓ | ✓ | ||
| Create custom incident actions | ✓ | ✓ | ||
| Add/edit/delete any: ∙ On-call schedules ∙ Schedule overrides ∙ Escalation policies ∙ Services ∙ Maintenance windows ∙ Teams ∙ Incident Workflows ∙ Business Services ∙ Business Services on incidents |
✓ | ✓ | ||
| Edit and update webhooks and extensions | ✓ | ✓ | ||
| View/edit/delete all private Teams and their services, schedules, and escalation policies across the entire account | ✓ | ✓ | ||
| Create/delete global API access key/token | ✓ | ✓ | ||
| ∙ Manage users ∙ Add new users ∙ Delete users ∙ Edit users’ profiles and passwords ∙ Configure users' base roles, Team roles, and object roles |
✓ | ✓ | ||
|
∙ Redact Incidents ∙ Administer the account ∙ Change the account owner ∙ Edit billing information ∙ Add/edit/delete single sign on (SSO) properties ∙ Delete the account ∙ Change pricing plans |
✓ |
* Limited Stakeholder and Full Stakeholder subscriptions to internal status pages are only available on the following pricing plans: Business, Digital Operations (legacy) and Enterprise for Incident Management. Please contact our Sales Team if you would like to upgrade to a plan with this feature. Note: These roles can only subscribe to prioritized incidents appearing on internal status pages.
Team Responder Base Role (Legacy)
The Team Responder base role was deprecated on April 26, 2019. All users with this role have now been changed to an Observer base role and their Team roles will stay the same.
Full Stakeholder Users
Stakeholders can view objects in an account, but cannot make modifications. The intended use case for a Stakeholder is to add them as an incident Subscriber. Stakeholders will receive updates about incidents they have subscribed to, but cannot take any action.
Stakeholder users are available by default on our Digital Operations (legacy) and Enterprise for Incident Management plans, and can be purchased as add-on users on Professional and Business plans. Stakeholder licenses are not billed the same as full users. Please contact your account representative for more information.
Limited Stakeholder Users
Limited Stakeholders can view and subscribe to internal status pages, and view their user profile. Limited Stakeholders cannot view any other parts of PagerDuty, whether they are using the web app or the mobile app. This access level is great for users who don't need to see all of the alerts, schedules, and responder details in your account. Incident subscriptions are only available for Limited Stakeholders on our Business, Digital Operations (legacy) and Enterprise for Incident Management plans. Please contact our Sales Team if you would like to upgrade to a plan with this feature.
Team Roles
When you add a user to a Team, they will also be given a Team role. A user’s Team role indicates the level of access that they have to objects associated with that specific Team. Users may also have a primary Team, which some organizations may need for billing purposes. Please read our section Manage Primary Team for more information.
To find your own Team role, navigate to User Icon My Profile Permissions & Teams tab.
There are three types of Team roles:
| Observer | Responder | Manager | |
|---|---|---|---|
| View configuration objects and incidents associated with their Team | ✓ | ✓ | ✓ |
| When assigned to an incident, or added as a Responder: Can respond to, acknowledge, and reassign the incident | ✓ | ✓ | ✓ |
| Respond to incidents associated with their Team | ✓ | ✓ | |
| Trigger incidents for their Team | ✓ | ✓ | |
| Create/delete overrides on schedule associated with their Team | ✓ | ✓ | |
| Add/edit/delete schedules, escalation policies, services and maintenance windows associated with their Team | ✓ | ||
| Add existing users to their Team | ✓ | ||
| Edit and delete their Team | ✓ | ||
| Edit and update webhooks and extensions | ✓ |
When you add a user or assign them to a Team for the first time, their default Team role will depend on their base role. You can add users to a Team manually, or automatically when their escalation policy has an associated Team.
| Base Role | Default Team Role When Added to a Team |
|---|---|
| Observer* | Observer |
| Stakeholder | Observer |
| Restricted Access* | Observer |
| Responder* | Responder |
| Manager* | Manager |
| Global Admin | Manager |
| Account Owner | Manager |
* Administrators can adjust users’ default Team roles to grant them more or fewer permissions on a specific Team.
Object Roles
Objects roles are levels of access given for specific configuration objects (a schedule, escalation policy, and/or service) to an individual user. To find your own object-level role(s), navigate to User Icon My Profile Permissions & Teams tab.
There are three types of object roles:
| Schedule | Escalation Policy | Service | |
|---|---|---|---|
| Observer | Can view | Can view | Can view and add notes to incidents triggered on this service |
| Responder | Can view schedules and create/delete overrides | Can view | Can view and respond to incidents triggered on this service |
| Manager | Can edit schedule and create/delete overrides | Can edit | Can edit, set maintenance windows, and respond to incidents triggered on this service |
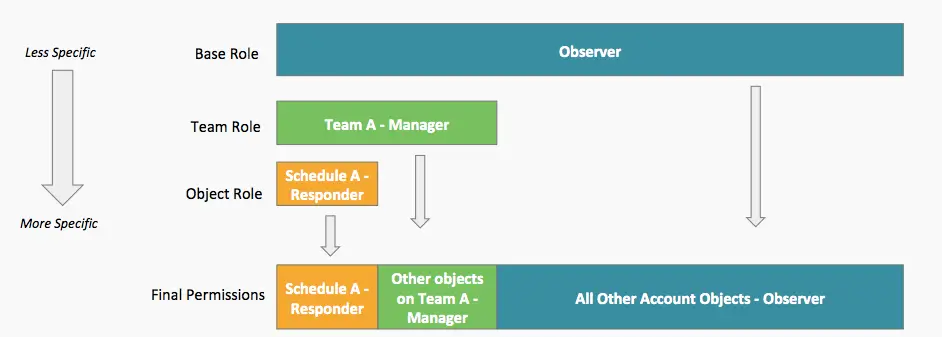
How Base, Team, and Object Roles Work Together
Base roles establish the level of access that a user has to everything across the entire account. In addition, Team and object roles give users more or less access to specific objects (i.e., schedules, escalation policies, services) and incidents than their base role alone would allow.
Manage Roles
Please see our Manage Users article for more information on managing Advanced Permissions user roles.
Team Privacy
With Advanced Permissions, Teams can be set to Private or Public. Please read our Teams article for more information on Team privacy.
Respond to Incidents From Other Teams
Please read our Teams article for more information on responding to incidents from other Teams.
Migration Role Mapping
When an account migrates from Basic to Advanced Permissions, most basic user roles are automatically mapped to Advanced Permissions base roles.
| Basic Permissions | Advanced Permissions |
|---|---|
| Account Owner | Account Owner |
| Admin | Global Admin |
| Stakeholder | Stakeholder |
| User | Manager |
| Limited User | Responder |
Note
Please note that there is no Observer role with Basic Permissions.
Roles in the REST API and SAML
When you provision a user through the REST API or SAML, the user will have the Manager (i.e., user) role by default, unless specified in the user's role property. The value must be one of a set of fixed values that our internal APIs recognize. Invalid requests will receive a response with the status 400 Invalid Request.
Values for user records’ role field correspond with role types above:
| Role Name | Value | Role Type |
|---|---|---|
| Global Admin | admin | Fixed |
| Full Stakeholder | read_only_user | Fixed |
| Limited Stakeholder | read_only_limited_user | Fixed |
| Manager / User | user | Flexible |
| Responder | limited_user | Flexible |
| Observer | observer | Flexible |
| Restricted Access | restricted_access | Flexible |
| Account Owner * | owner | Fixed |
* You cannot create this role through the REST API or SAML provisioning.
Updated 2 months ago
